Sandboxing For Mac

Sandbox For Mac Os X
You noticed something called “sandboxd” while looking through, and now you’re here. So what is this thing? RELATED: This article is part of explaining various processes found in Activity Monitor, like,. Don’t know what those services are?
Sandboxing Macos

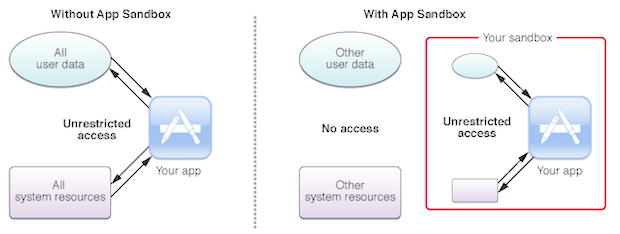
Better start reading! Today’s process, sandboxd, is a daemon, which means it runs a system task in the background on macOS—daemons generally have a “d” at the end of their name. This particular daemon handles the macOS sandbox, as running man sandboxd in your Terminal will show you: sandboxd performs services on behalf of the Sandbox kernel extension. RELATED: So what’s a sandbox? You can check out for an overview, but for the most part a sandbox prevents applications from accessing parts of the system it doesn’t need. The macOS sandbox is outlined on: App Sandbox is an access control technology provided in macOS, enforced at the kernel level. It is designed to contain damage to the system and the user’s data if an app becomes compromised.
Sandboxing On Mac
Before sandboxing, every application had access to everything the user did. This was nice for simplicity’s sake, but it meant every single application was a potential path to all of your data and hardware. Applications running in the sandbox have to specifically request access to things like your files or your webcam, giving you an added level of security. The macOS sandbox optionally can be implemented by applications you download online, but is mandatory for any application you download from the Mac App Store. This is just one reason. The process sandboxd probably shouldn’t be taking up much of your system resources, but if it does try shutting down any recently installed applications. If that solves the problem, consider submitted a bug report to the developer, because something about that application is causing problems.